Test News
This is a sample news post
Read More
The age of mass data creation demands new standards for data privacy and security.

Throughout history, emerging technologies have typically experienced exponential growth before the introduction of safety standards. Those standards tend to be based on difficult lessons learned. For example, building skyscrapers with little regard for worker safety prior to OSHA or automobiles before airbags, anti-lock brakes and speed limits.
Data and technology solutions are now experiencing a similar shift with the overlay of data privacy. 2.5 quintillion bytes of data are created each day. That pace is only accelerating with the growth of new technologies, such as Internet of Things (IoT), data sensors, and artificial intelligence.
This data can be incredibly helpful. It can enable organizations to better understand who you are as a consumer: your likes, preferences, dislikes, and the types of products you have higher propensity to buy. So, in general, this data can help create a better experience with the brands that you interact with daily. However, the yin to the yang of this scenario is that organizations have deep information relating to you as a person.
The challenge isn’t simply having the data — it’s protecting it. If your IT network is antiquated, with too many tools, APIs, and third-party vendors, it is a good target for hackers or other cyberattacks. According to Gartner, 270 attacks per year per company are due to network inefficiencies and 61% of network security breaches are through third-party vendor network endpoints.
If your organization falls into the buckets below, securing your network becomes paramount to protect your organization from cybercrime.
According to Gartner and Spotlight:
The new privacy laws going into effect help organizations inventory their employee and customer data while specifying access and control rights, however, they are not targeted at protecting data from security breaches.
To deal with these challenges, varying industries have taken steps to clearly outline how data should be protected in terms of privacy and security; interrelated but not synonymous topics.
Much of this has been effective in helping to prevent catastrophic data leaks and in giving people more peace of mind regarding their data. However, these rules and regulations can lead to negative financial or reputational repercussions if not properly instituted or managed.
Examples of significant data leaks:
So, the question is: What can organizations do to protect consumer data; take on the true role of data “processor” and not the data “controller” to create consumer trust; and ultimately protect their brand in the process?
As defined by the European Commission:
The data controller determines the purposes for which and the means by which personal data is processed.
The data processor processes personal data only on behalf of the controller. The data processor is usually a third party external to the company.
Data Security is defined by three key principles:
These principles are critical sister topics to Data Privacy.
The principles of GDPR are built around giving a person the right to control their data and to remain anonymous. The mechanisms by which this occurs is a unified European Union policy that allows consumers to request that entities Provide (access to), Delete or Change their personal information.
This European model was mimicked by the State of California, who signed into law the CCPA which went into effect on January 1, 2020. This legislation broadened the definition of Personal Information (“PI”) from that of Personally Identifiable Information (“PII”) and gave consumers the right to request that entities Provide or Delete, but not Change information. Furthermore, it allows consumers to Opt-Out of allowing businesses to use their information. California began enforcing this law on July 1, 2020.
Beyond California, Colorado, Connecticut, Rhode Island, Utah, and Virginia have passed comprehensive data privacy laws. Other states, including Nevada and Maine have passed legislation to enable customers to Opt-Out and Opt-In, respectively, of data use. In addition, legislation is being crafted in New Jersey, Pennsylvania, Ohio, and Michigan. Hence, there is quite a bit of activity in this area for which organizations need to plan and prepare.
RevGen recommends conducting an assessment of your organization’s Data Privacy Strategy, as well as the your technology stack, including API’s and third-party connections to secure all your employee and customer data.
While every organization’s approach to managing data privacy requirements will vary based on size and the complexity of the operations and systems, all approaches will have a degree of complexity because data privacy cuts across the entire enterprise from a people, process, and technology standpoint.

RevGen believes companies need to determine how they plan to build or deploy their data privacy solutions. These solutions can be high risk if not looked at holistically, given the potential for negative brand exposure and fines. In addition, they can span the entire value delivery chain; meaning they are consumer facing, spiderweb into each business unit, and require secure output on the backend.
Choosing the right technical solution also is crucial to protecting this data from potential security breaches. It is critical to build a holistic plan to protect your data.
As for building the technical solution to manage data privacy, various options should be explored:
One of the biggest Data Privacy challenges is simply locating and documenting where Personal Information exists. On the surface, this sounds like a straightforward activity, but when you drill into it, companies will quickly find that they must first:
A miss on this front puts the entire effort at risk.
However, ensuring compliance with Data Privacy laws isn’t enough, as none of them specify security measures that should be taken to protect an organization’s network from the very real threat of cybercrime. It’s important to remember that the technical solutions you choose should encompass these needs as well.
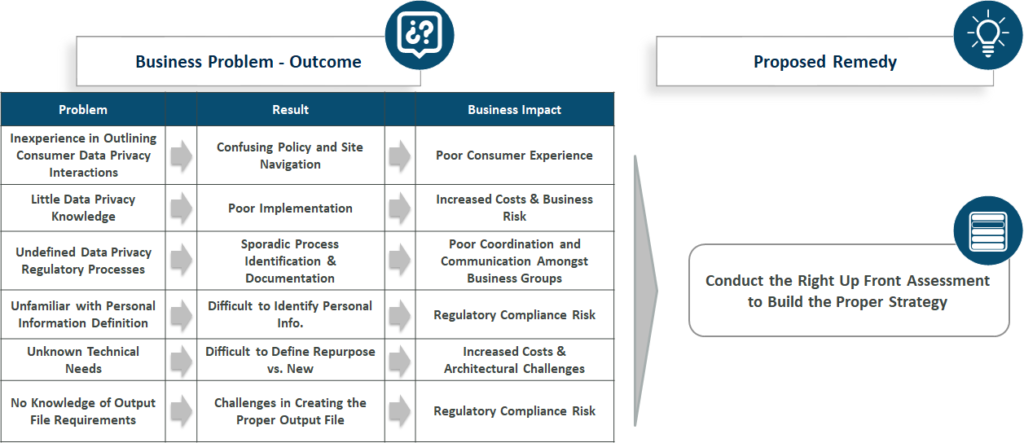
We understand that many organizations may not be immersed in all of the changing regulations or have an internal team skilled in these types of programs, so this may be the time to consider bringing in external Data Privacy expertise to help facilitate your journey. And, as with any cross-functional, enterprise-wide program, process design, program management and change management must all be considered. The risks of not doing so are shown below.
Proper program governance can help keep the Total Cost of Ownership of the program as low as possible while decreasing overall risk. Lastly, it will ensure requirements are properly translated into a comprehensive solution deployment in what is a high stakes environment.
In closing, data privacy is a burgeoning area which RevGen Partners believes organizations would be wise to get out in front of, especially given the increase in data privacy laws and rising numbers of cyberattacks. All breakthrough technologies eventually require adjustments in their management to ensure safety for your employees, your customers, and your organization.
If your organization needs support for your Data Privacy projects visit our site to learn more.
Get the latest updates and Insights from RevGen delivered straight to your inbox.